Fascination About S3 Backup
Wiki Article
All about Ransomware Protection
Table of ContentsSee This Report about Aws S3 BackupA Biased View of Aws BackupMore About Ransomware ProtectionS3 Backup - The FactsThe smart Trick of Aws Backup That Nobody is Talking AboutExcitement About Protection Against Ransomware
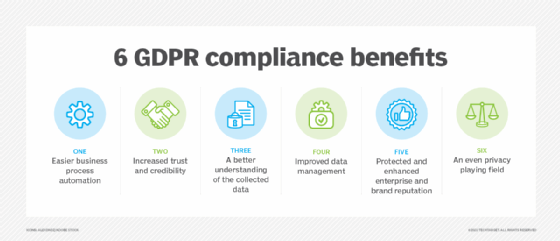
Global authorities have actioned in with governing compliance like General Data Protection Guideline (GDPR). The GDPR stresses the personal information legal rights of EU residents, consisting of the right to change, access, erase, or transfer their information. Personal information refers to any details that relates to an individual. This consists of names, physical characteristics, addresses, racial or ethnic features, and also biometric information like DNA as well as fingerprints.
To keep their information available in all times, companies need to maintain the IT framework active even in the instance of a disaster. This state of guaranteed access to information is called data schedule. This post examines the essentials of data availability and also its challenges, as well as supplies strategies to maintain a high level of data availability.
Without a proper information safety plan, sensitive information can come under the hands of assailants, enabling them to gain accessibility to your network, and also reveal the individual info of consumers and also staff members. This post presents the idea of data security as well as the various devices and also techniques you can utilize to secure your data and stop a catastrophe.
Not known Facts About Aws Cloud Backup
The encoded details can only be translated with a special decryption trick. You can generate the key either at the time of security or in advance. File encryption ensures the honesty of data by securing it from unapproved alteration. Security lowers the danger of accessing information from untrustworthy sources by confirming information's source.A constant information protection system keeps a document of all data changes and also enables you to bring back a system to any kind of previous moment. This sort of back-up solves the issue of shedding data developed between two scheduled backups. It likewise gives protection against attacks like ransomware or malware, along with unexpected removal of information.
Any company that processes and also shops individual information of EU people, even if it is not physically located in the EU, have to apply to the GDPR regulations. There are 2 main functions in the GDPR: the GDPR Data Cpu is an entity that holds or processes this sort of data in behalf of one more organization, and a GDPR Information Controller that collects or refines individual data for its very own purposes.
Object Lock avoids item version deletion throughout a user-defined retention period. Immutable S3 objects are protected making use of things, or bucket-level arrangement of WORM and also retention features. This capability provides both data defense, consisting of additional security against unintended or destructive deletion in addition to ransomware and governing conformity. Find out more: S3 Things Lock Protecting Data for Ransomware Hazards and also Conformity The cloud-based subscription of Office 365 makes it possible for staff members to function anywhere, anytime without the demand to hold their very own web content and also e-mails.
The Of Aws S3 Backup
Information protection is the process of guarding crucial info from corruption, concession or loss. The significance of data protection increases as the amount of information developed as well as saved remains to grow at unmatched prices. There is likewise little tolerance for downtime that can make it difficult to accessibility important details.

The essential principles of data security are to secure as well as make offered information under all situations.
The Definitive Guide for Aws Cloud Backup
Information lifecycle management is the process of automating the activity of critical data to online and offline storage. Info lifecycle administration is a thorough method for valuing, cataloging as well as safeguarding info assets from application as well as user mistakes, malware and also infection strikes, maker failure or center blackouts as well as disruptions. Extra recently, information management has pertained to consist of locating methods to open company worth from or else inactive duplicates of information for reporting, test/dev enablement, analytics and also various other purposes.(CDP) backs up all the information in a venture whenever a modification is made. Data mobility-- the ability to move information among various application programs, calculating environments or cloud services-- presents an additional collection of problems and options s3 cloud backup for data protection.
The smart Trick of S3 Cloud Backup That Nobody is Talking About
Information defense is the process of securing important info from corruption, compromise or loss. The importance of data defense increases as the amount of information created and also kept remains to grow at extraordinary rates. There is likewise little tolerance for downtime that can make it difficult to accessibility vital details (https://is.gd/5BMgTC).Protecting information from compromise as well as making sure data personal privacy are other crucial components of information defense. The coronavirus pandemic caused countless employees to function from house, resulting in the need for remote data security. Businesses should adjust to ensure they are protecting data anywhere workers are, from a central information facility in the workplace to laptops in the house.
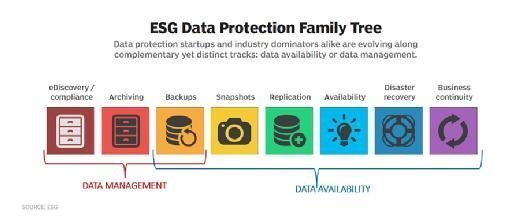
The essential principles of information security are to secure and also offer data under all circumstances. The term data security describes both the operational backup of information in addition to company continuity/disaster recuperation (BCDR). Information defense strategies are evolving along two lines: information accessibility as well as data administration. Data accessibility makes sure individuals have the data they require to perform service also if the data is harmed or shed.
Details lifecycle management is a detailed technique for valuing, cataloging and securing details possessions from application as well as customer mistakes, malware and virus assaults, equipment failing or center failures as well as disturbances. Much more recently, data monitoring has come to consist of finding means to open business worth from otherwise inactive duplicates of information for coverage, test/dev enablement, analytics as well as various other objectives.
4 Easy Facts About Aws Cloud Backup Explained
(CDP) backs up all the information in a business whenever a change is made. Information portability-- the capacity to relocate information amongst various application programs, calculating settings or cloud services-- offers one more collection of troubles as well as services for information defense.Report this wiki page